Understanding what Is public Key is a core concept in modern digital security and Cryptocurrency systems. A public key allows people and systems to exchange information safely over open networks like the internet. Without it, secure digital communication would be far more difficult. As online transactions, digital wallets, and blockchain networks continue to grow, public keys play an even bigger role in protecting users and assets.
In the crypto space, a public key is closely linked to ownership and identity. It allows users to receive funds, verify transactions, and prove authenticity without exposing private information. This balance between openness and security is what makes public key cryptography so powerful. It supports trust in systems where users may not know or trust each other.
In this article, you will learn what a public key is, how it works, where it came from, and how it is used today. The guide also covers types, advantages, disadvantages, and real-world applications in a clear and practical way.
What Is Public Key?
Public Key refers to a cryptographic value that is shared openly and used to encrypt data or verify digital signatures. It works as part of a pair called asymmetric cryptography. The pair includes it and a private key. While this can be shared with anyone, the private key must remain secret.
The main purpose of a it is to allow secure interaction without exchanging secret information first. When someone wants to send encrypted data, they use the recipient’s public key. Once encrypted, the data can only be decrypted using the matching private key. This design prevents unauthorized access, even if the data is intercepted.

Public keys also help confirm identity. When a message or transaction is signed with a private key, others can use the public key to verify that it came from the correct source. In blockchain networks, this process supports transparency, trust, and secure ownership without relying on central authorities.
Background of Public Key
To fully understand Public Key, it helps to look at the structure and elements that support it. It’s cryptography relies on complex mathematical functions that are easy to compute in one direction but extremely difficult to reverse. This one-way nature is what makes the system secure.
Each of it is mathematically linked to a private key. Although they are related, knowing the it does not reveal the private key. This separation allows open sharing while maintaining security. This systems also depend on standardized algorithms that have been tested and reviewed over many years.
Key features make public keys reliable and widely adopted. These features work together to protect data, verify identity, and secure transactions across digital platforms.
List of Key Components or Aspects:
- Public key used for encryption or address generation
- Private key used for decryption and signing
- Asymmetric cryptographic algorithms
- Digital signatures for verification
- Hash functions to maintain data integrity
Each component plays a specific role. Together, they form the foundation of secure digital communication.
History of Public Key
The idea behind Public Key emerged from a long-standing problem in cryptography. Before public key systems, secure communication required both parties to share the same secret key in advance. This approach did not scale well, especially for large networks.
In the mid-1970s, researchers proposed a new solution. They introduced the concept of asymmetric cryptography, where two different but related keys could be used. This breakthrough changed how secure communication worked. Shortly afterward, practical algorithms were developed that made public key systems usable in real-world environments.
Over time, Its cryptography became a standard part of internet security. It later became essential to blockchain and digital asset systems, where trustless interaction is a key goal.
| Year | Milestone |
|---|---|
| 1976 | Concept of public key cryptography introduced |
| 1977 | First widely used public key algorithm developed |
| 1990s | Adoption in web and email security |
| 2009 | Use in blockchain and decentralized networks |
Types of Public Key
There are several types of Public Key, each based on different mathematical methods. Although the goal is the same, the way each type achieves security varies.
RSA public keys are one of the oldest and most widely known types. They rely on the difficulty of factoring large numbers. While secure, they often require longer key sizes, which can reduce efficiency. Elliptic Curve public keys offer a more modern approach. They provide strong security with much shorter keys, making them faster and more efficient.
Some public keys focus mainly on encryption, while others are optimized for digital signatures. In blockchain systems, public keys often generate wallet addresses rather than being used directly. Each type is chosen based on the system’s performance, security needs, and design goals.
How Does it Work?
The process behind it follows a clear and logical flow. First, a user generates a key pair using cryptographic software. This step creates both a public key and a private key at the same time. Next, this is shared openly, while the private key is stored securely.
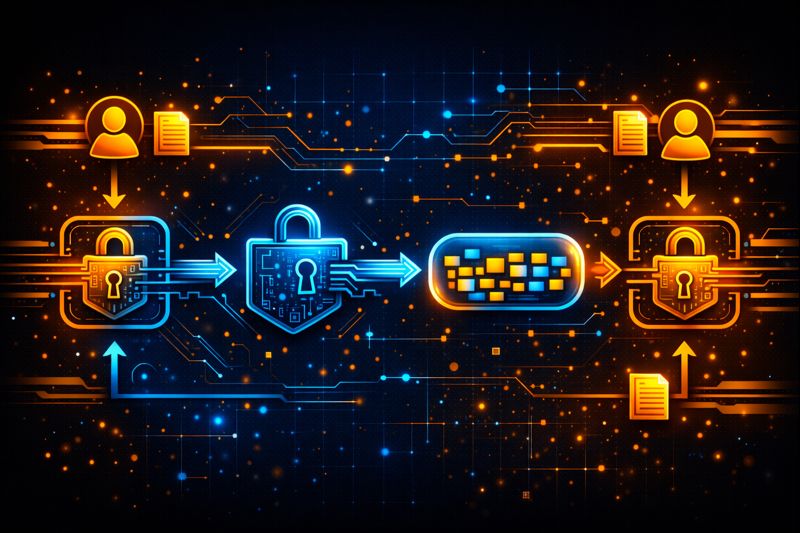
When someone wants to send encrypted data or digital assets, they use this. The system encrypts the data so that only the matching private key can unlock it. Even if the encrypted data is intercepted, it remains unreadable to outsiders.
In verification scenarios, the process works in reverse. A private key signs a message, and others use the this to confirm its authenticity. This mechanism supports secure transactions, ownership proof, and trustless Trading environments.
Pros and Cons
Like any technology, it comes with strengths and weaknesses. Understanding both helps users and developers apply it correctly.
| Pros | Cons |
|---|---|
| Enables secure communication over open networks | Slower than symmetric encryption |
| Eliminates the need to share secret keys | Key management can be challenging |
| Supports identity verification and signatures | Loss of private key means permanent loss of access |
Despite its drawbacks, the benefits often outweigh the limitations, especially for systems that require high security and transparency.
Uses of Public Key
The real-world uses of it are widespread and continue to grow. In Cryptocurrency networks, public keys help generate wallet addresses and verify transactions. They ensure that only the rightful owner can access funds while allowing anyone to view transaction data.
Email encryption systems rely on public keys to protect messages and confirm sender identity. Secure websites use them to establish encrypted connections between browsers and servers. Software developers also use public keys to verify updates and prevent tampering.
Financial platforms, identity systems, and decentralized applications all depend on public key cryptography. As digital interactions increase, public keys remain a cornerstone of secure and reliable technology.
Resources
- Blockchain.com: How Wallets Work
- CoinDesk: Crypto Wallets Explained
- Ethereum.org: Keys & Addresses
- Coinbase Learn: Private vs Public Keys
- Gemini Trust: Keys

